
Josh Duggar isn’t the only person who is going to have his or her life turned upside down by the Ashley Madison hack and data dump. A second leak has been released, and the legal troubles for everyone involved are only getting started.
The Associated Press traced many of the accounts exposed by hackers back to federal workers.
They included at least two assistant U.S. attorneys; an information technology administrator in the Executive Office of the President; a division chief, an investigator and a trial attorney in the Justice Department; a government hacker at the Homeland Security Department and another DHS employee who indicated he worked on a counter-terrorism response team.
AP traced their government Internet connections — logged by the website over five years — and reviewed their credit-card transactions to identify them. They included workers at more than two dozen Obama administration agencies, including the departments of State, Defense, Justice, Energy, Treasury, Transportation and Homeland Security. Others came from House or Senate computer networks
And this particular leak seems to have been specifically designed to prove to Ashley Madison CEO Noel Biderman that the hackers do indeed have access to everything.
The new documents were dumped with a taunting message to the adultery website’s founder as exposed users began to publicly admit their involvement.
‘Hey Noel, you can admit it’s real now,’ read the post – presumably directed at the company’s millionaire CEO Noel Biderman, who has refused to admit the material is all legitimate.
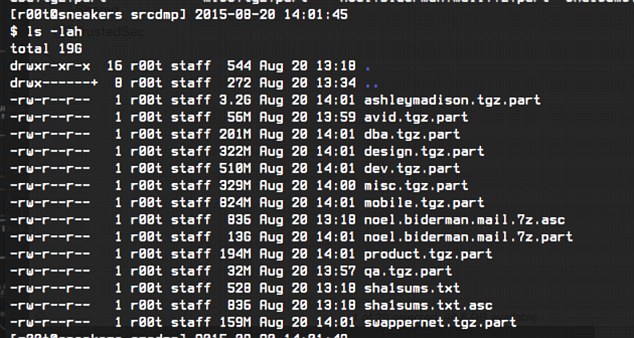
The second (data leak) appears to include personal information and emails of the CEO with folders entitled Noel Biderman.mail.
Other folders are titled mobile, product and design.‘The dump appears to contain all of the [CEO’s] business/corporate e-mails, source code for all of their websites, mobile applications, and more,’ researchers from TrustedSec wrote in a blog post published Thursday.
Another document shows the website were aware of the privacy dangers and discussed a potential security breach.
A file called ‘Areas of concern – customer data.docx’ a worker flagged potential hacking hazards.
And while the hackers are reveling in the chaos, Ashley Madison is also being forced to admit that they don’t verify email addresses and apparently never deleted anyone’s profiles.
Only 2.3 million are considered ‘active’ users of the site but the hack includes names and details of anyone who has ever registered – even if they didn’t use the services to have a full-blown affair or quit their philandering ways years ago.
Up to 15,000 names among the raw data are listed from email addresses with the domain names .mil or .gov – the official addresses of U.S government and military employees.
Ashley Madison admits it doesn’t verify email addresses so some are known fakes.
Barack Obama and Tony Blair are among the fake names and email addresses that have already been exposed. However, several emails are legitimate.
But for those who used a government work email, this might be only the beginning of their troubles.
Defense Secretary Ash Carter confirmed Thursday the Pentagon was looking into the list of people who used military email addresses. Adultery can be a criminal offense under the Uniform Code of Military Justice.
“I’m aware of it,” Carter said. “Of course it’s an issue because conduct is very important. And we expect good conduct on the part of our people. … The services are looking into it and as well they should be. Absolutely.”
A White House spokesman said Thursday he could not immediately comment on the matter. The IT administrator in the White House did not return email messages.
While rules can vary by agency, Homeland Security rules, for instance, say devices should be used for only for official purposes. It also prescribes “limited personal use is authorized as long as this use does not interfere with official duties or cause degradation of network services.” Employees are barred from using government computers to access “inappropriate sites” including those that are “obscene, hateful, harmful, malicious, hostile, threatening, abusive, vulgar, defamatory, profane, or racially, sexually, or ethnically objectionable.”
The real concern, of course, is the potential for blackmail that would exist for anyone in a sensitive area of government who could be identified. And of course, Ashley Madison and CEO Noel Biderman are in a world of legal trouble if they knew that their data could be breached and did nothing about it.
There are no winners here, mostly because everyone involved, to some degree, is a loser. There are real people behind the email addresses whose lives are being destroyed because of their actions. There’s a company who advertised themselves as a secret place to cheat, and then didn’t secure their data well enough. And then there are the hackers, who are almost gleeful about what they have done, but still committed a crime in hacking and stealing personal data. What a sorry, sordid mess.
So some of these wonderful folk have been fooling around on the government dime? That figures. What a classy bunch we have in DC-they could at least have the decency to get on that site at home.
Better yet-why the hell wasn’t this site blocked at government offices? I doubt I can access that site where I work as even Facebook is blocked. Makes you wonder what other unblocked sites the nomenklatura have access to
for their leisure that most normal companies would block.
1 Comment